If you are a cybersecurity enthusiast, then you must have heard of YARA. It’s a powerful tool, a veritable magnet for digital threats. Today, we dive into how this powerful tool can be used to hunt down phishing kits and phishing pages.
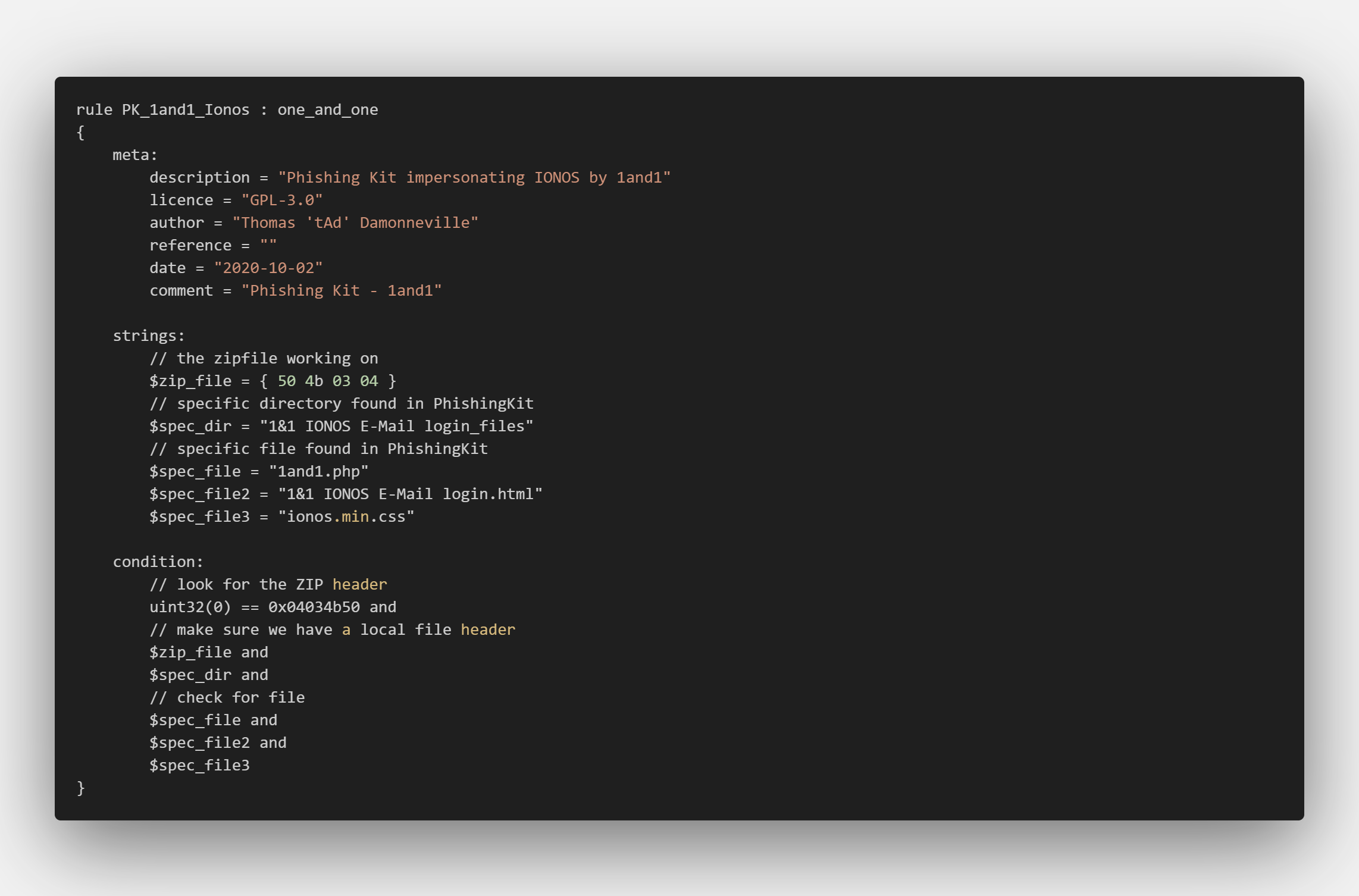
YARA Rule Overview: PK_1and1_Ionos
This YARA rule, named “PK_1and1_Ionos“, is designed to detect a phishingkit that impersonates IONOS by 1&1, a well-known web hosting company. Authored by Thomas ‘t4d’ Damonneville, it’s an excellent example of how YARA can be used to detect and neutralize these digital dangers.
Deciphering the Code

So, what’s going on in this rule? Let’s break it down:
- The ‘meta’ section provides important information about the rule, including a description, author, and the date it was created. It’s like the rule’s ID card.
- The ‘strings’ section is where the magic happens. These are the specific patterns that YARA will search for. In this case, we’re looking for a ZIP file (
$zip_file), a specific directory ($spec_dir), and specific files ($spec_file,$spec_file2, and$spec_file3). These are all key identifiers of the phishingkit. - Finally, the ‘condition’ section tells YARA when to raise the alarm. It’s essentially saying: “If you find these specific patterns, then we’ve got a match!”
Phishingkit Hunting in Action
When you run this YARA rule, it scans files for the specific patterns defined in the ‘strings’ section. The moment it detects a ZIP file that contains the specific directory and files, it flags it as a match. It’s like a hound dog sniffing out a truffle – once it gets a whiff of the specific scent (or in this case, patterns), it knows it’s found its target.
But Reza, you just showed us one example
Yes, that is true, as there is a massive Github repository containing numerous YARA rules that can detect phishing kits and phishing pages.

So What Do I Need To Get Results?
To successfully hunt for phishingkits and phishing pages using YARA, you’ll need a few crucial elements. Think of these as the key ingredients in your cybersecurity recipe.
Feed of Potential Phishing Kits or Phishing Pages
The first item you’ll need is a feed of potential phishing kits or phishing pages. This is essentially your data source that you’ll be analyzing. You can think of it like the fuel for your YARA engine. You can collect these potential threats from various sources, like suspicious emails, reported phishing URLs, or even dark web marketplaces where these kits are sold.
A System to Run YARA and the Signatures
Next up, you need a system that can run YARA and the signatures. This is where the magic happens. The system will apply the YARA rules (like the PK_1and1_Ionos rule we discussed earlier) to the feed of potential phishingkits and pages, sifting through the data to spot any matches.
A Separate Folder for Potential Phishing Kits and Pages
You’ll also need a separate folder where you can store potential phishing kits and pages for further analysis. This will serve as a ‘holding area’ for any matches YARA finds. From here, an analyst can then dive deeper, examining the flagged items in detail to confirm whether they are indeed phishingkits or phishing pages.
Additional Tools for Finding Potential Phishing Resources
Finally, using tools like URLscan.io can be extremely beneficial in your hunt for phishing resources. URLscan.io is a service that scans and analyzes websites, sniffing out any potentially malicious activity.
Moreover, keeping track of your Apache logs or other server logs can provide valuable clues about suspicious activity. This can help you spot potential phishing resources that might have otherwise flown under the radar.
You might want to read:
- Guide: YARA Detection for Sliced Strings
- YARA Rules 101: Quickly craft YARA rules
- Top 25 Open Source Cyber Security Tools
By bringing these elements together, you can effectively use YARA to hunt for phishingkits and phishing pages. Remember, cybersecurity is all about being proactive and staying one step ahead of the threats. Happy hunting!
Done reading? Continue with The YARA User Guide: How to Install and Scan for .onion Strings.