Search results for: “cyberattack”
Showing results matching your search
Refine your search
-
The 2007 Estonia Cyberattacks and How They Shaped Modern Cyber Defense
The 2007 cyberattacks against Estonia disrupted banks, media, and government systems and reshaped NATO cyber defense policy, turning Estonia into a global cybersecurity leader.
·
·
16–24 minutes -
JLR cyberattack: 43% drop in wholesale volumes
JLR cyberattack halted production, cutting Q3 wholesale volumes 43% and costing ~£196M.
·
·
1–2 minutes -
German City of Ludwigshafen Suffers Cyberattack, Systems Offline
The German city of Ludwigshafen has taken its ICT systems offline after a cyberattack, disrupting public services and highlighting the vulnerability of critical municipal infrastructure. The incident is under investigation, mirroring a global trend of…
·
·
1–2 minutes -
Australian Signals Directorate Warns of Ongoing BADCANDY Cyberattacks on Cisco IOS XE Devices
The Australian Signals Directorate (ASD) has issued a bulletin regarding ongoing cyberattacks targeting unpatched Cisco IOS XE devices in Australia, utilizing a previously undocumented implant identified as BADCANDY. These attacks exploit CVE-2023-20198, a critical vulnerability…
·
·
2–4 minutes -
Dutch rail watchdog warns of weak defences against sabotage and cyberattacks
The Overlegorgaan Fysieke Leefomgeving warns the Dutch rail network remains vulnerable to sabotage and cyber threats, urging tighter defence coordination.
·
·
1–2 minutes -
What Is Cyber Warfare? Definition, Doctrine, and Real-World Examples
Cyber warfare refers to state-driven digital operations designed to disrupt, spy on, or damage an adversary’s infrastructure, military systems, or decision-making capabilities.
·
·
14–21 minutes -
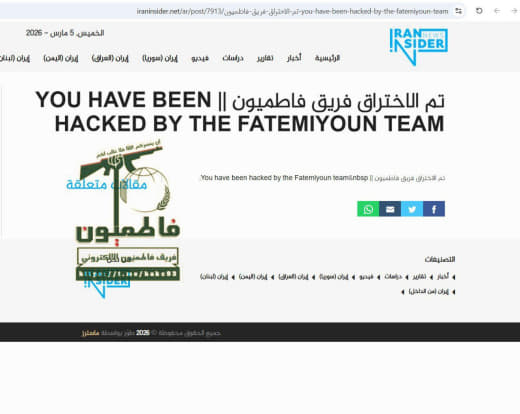
Fatimion Cyber Team: Inside the Iran-Linked Hacking Group Waging Cyber War Across the Middle East
A pro-Iran cyber group operating out of Iraq has quietly built one of the most persistent hacktivist operations in the Middle East. Known as the Fatimion Cyber Team (فريق فاطميون الالكتروني), this group has been…
·
·
14–22 minutes -
Cyber & Electronic Warfare · Cyber News & Updates · Digital Espionage & Intelligence · IranRevolution2026 · Operations & Campaigns
Iranian Revolution 2026: Complete Intelligence Briefing — Protests, War, Cyber Operations, and the Fall of Khamenei
Comprehensive intelligence briefing on the Iranian Revolution of 2026 — from the December 2025 protest eruption and regime massacres, through Operation Epic Fury and Operation Roaring Lion, the assassination of Khamenei, the Strait of Hormuz…
·
·
31–46 minutes -
UMMC ransomware attack forces closure of 35 Mississippi clinics
UMMC ransomware attack: University of Mississippi Medical Center closed all 35 statewide clinics after a ransomware infection took information systems offline, forcing cancellations of appointments and non‑urgent care.
·
·
2–3 minutes -
OpenAI leaks personal data and metadata of API users
OpenAI has disclosed a data leak affecting an undisclosed number of API users, with personal data and metadata exposed after an attack on its analytics provider, Mixpanel. The compromised data includes names, email addresses, location…
·
·
1–2 minutes