Search results for: “network security”
Showing results matching your search
Refine your search
-
Cisco Firepower Firewalls: Next-Gen Protection and Critical Vulnerabilities
This article examines Cisco Firepower Firewalls, detailing their next-generation protection capabilities and critical vulnerabilities. It highlights the importance of timely updates as warned by CISA for effective cybersecurity.
·
·
2–3 minutes -
Unnamed APT Exploits Zero-Days in Citrix and Cisco, Targeting Critical Infrastructure
An unnamed advanced persistent threat (APT) group exploited zero-day vulnerabilities in Citrix NetScaler ADC and Gateway, dubbed “CitrixBleed 2,” and a critical flaw in Cisco Identity Service Engine (ISE). The attacks targeted essential identity and…
·
·
2–3 minutes -
AI Weaponization: State Hackers Using Google Gemini for Espionage and Malware Generation
What Happened Google’s Threat Intelligence Group (GTIG) has confirmed that multiple state-sponsored hacking groups are actively using its Gemini large language model (LLM) to enhance their cyber espionage and attack capabilities. The activity spans reconnaissance,…
·
·
4–6 minutes -
Cloud-Native Attacks: TeamPCP Industrializes Worm for Ransomware and Data Theft
TeamPCP, a sophisticated cybercrime group, has launched a worm-driven campaign targeting cloud-native environments, including Docker APIs, Kubernetes, and Redis. Exploiting misconf
·
·
7–10 minutes -
D-Knife Spyware: China-Linked APT Hijacks Routers for Cyber Espionage
Unveiling the D-Knife spyware campaign, a sophisticated China-linked APT operation hijacking internet routers for persistent surveillance and data exfiltration. Discover its techni
·
·
1–2 minutes -
China-Linked UNC3886 Cyber Espionage Targets Singapore Telecom
China-linked APT UNC3886’s sophisticated cyber espionage against Singapore’s telecom sector highlights evolving nation-state threats to critical infrastructure, demanding executive
·
·
2–3 minutes -
Dutch Police Hack iPhones: Unpacking Real-Time Surveillance Capabilities
Recent reports from AD and Security.NL reveal that Dutch police have employed advanced hacking techniques to gain real-time access to suspects’ iPhones. This unprecedented level of surveillance allows law enforcement to monitor a suspect’s phone…
·
·
3–5 minutes -
Leaked Tasnim Memo Exposes IRGC Media Plan to Discredit Reza Pahlavi
A leaked Tasnim memo shows an IRGC-linked media plan to frame Iran’s protests as foreign-driven and discredit exiled Prince Reza Pahlavi. Analysis and practical takeaways.
·
·
2–3 minutes -
IRAN’S REGIME IS GETTING HACKED IN REAL TIME — AND THE 2026 REVOLUTION IS WATCHING
Iran’s 2026 uprising isn’t just happening in the streets anymore — it’s happening inside the regime’s own networks. And the Islamic Republic is losing hard. In a major digital strike, anti-regime hackers reportedly hijacked Iran’s…
·
·
1–2 minutes -
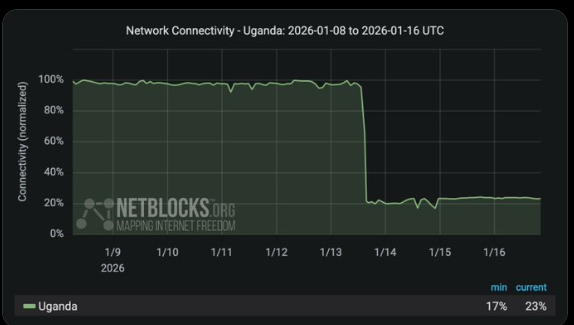
Uganda Elections 2026: Internet Shutdown Continues as Reports Emerge of Bobi Wine Abduction
A nationwide internet shutdown in Uganda remains firmly in place just past midnight, following restrictions imposed ahead of the country’s elections. The ongoing disruption continues to severely limit access to information and hamper independent verification…
·
·
1–2 minutes